
Configuring Squid, Apache and SARG
Now we need to configure everything.
Well start off with Apache.
Because we’re intercepting port 80 & 443, we’ll be
changing Apache’s default ports. Apache will be used to access SARG’s reports.
Type nano /etc/apache2/ports.conf and press
Enter.
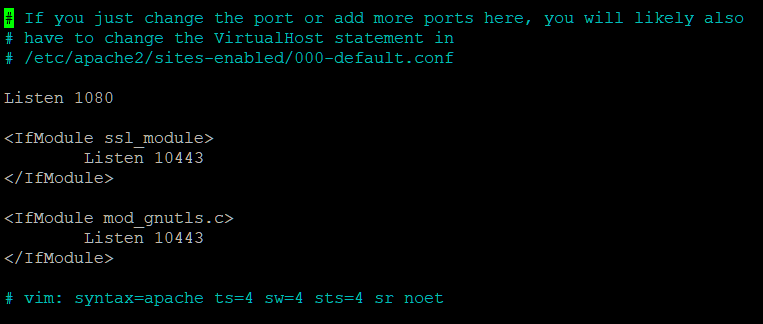
Change the values in the file so yours reflects the changes
above. Save and Exit.
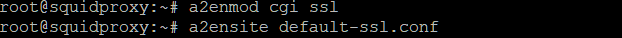
We also need to enable a few apache modules & the
default SSL site.
Next we need to create a directory for cgi scripts.
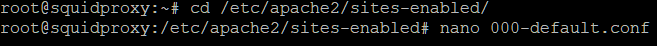
Now we need to configure the default sites to allow CGI
scripts.
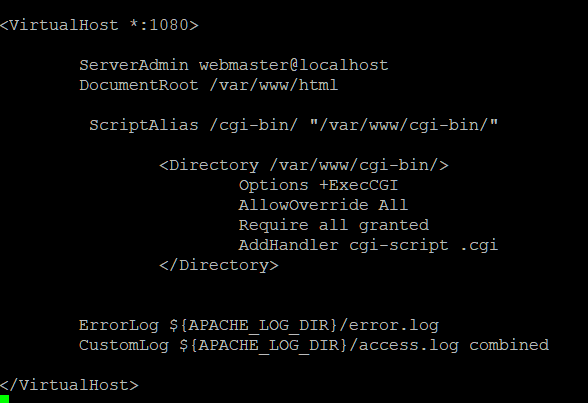
Delete or comment out the contents & replace with above.
Save & Exit.
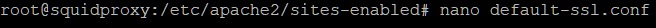
Next, the SSL site.
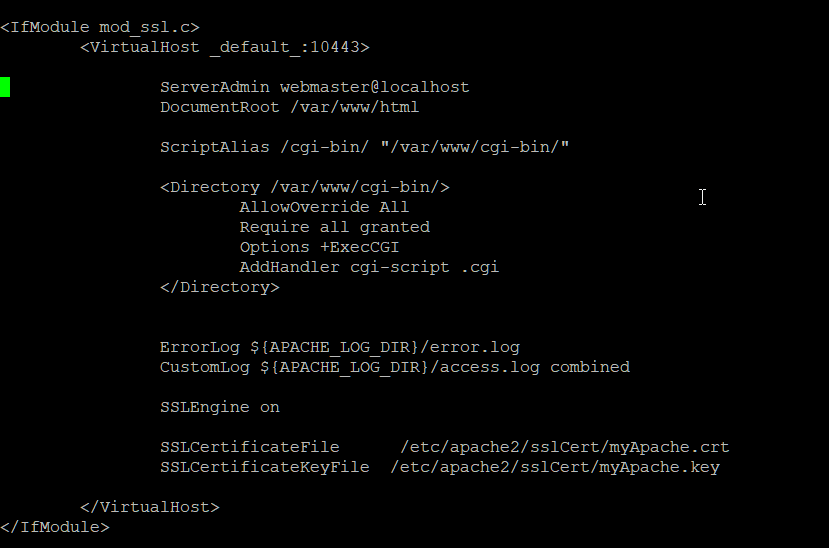
Delete or comment out the contents & replace with above.
Save & Exit.
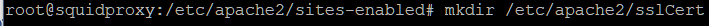
Next we need to create a directory to hold our SSL
Certificates for Apache’s SSL site.
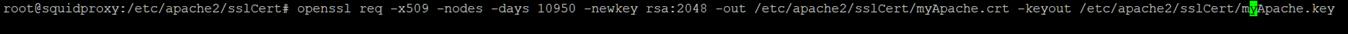
Then we need to generate the certificate. Fill out the
details requested. Days control how long the certificate is valid for, you’ll
have renew it when it expires.
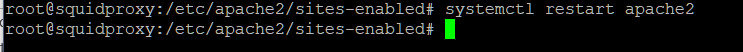
Now restart Apache.
Now we’ll configure SARG.
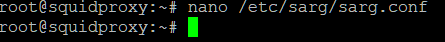
Type nano /etc/sarg/sarg.conf and press Enter.
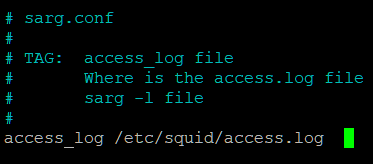
Find the line above and change the path to
/var/log/squid/access.log. Save and Exit.
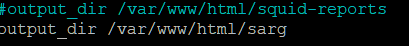
Find the line above, and change the path to
/var/www/html/sarg. Save & Exit.
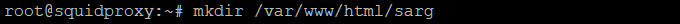
Next, create the report output_dir by typing mkdir
/var/www/html/sarg.
And finally, we need to configure Squid.
We first need to create our CA certiface for Squid and
export it to a format that can be imported on our users machines.
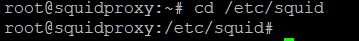
Change to the squid config directory with cd
/etc/squid/
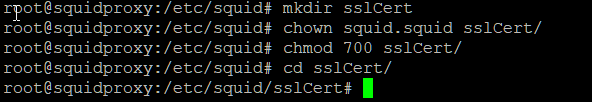
Execute the commands in the screenshot above.
Next to generate the CA Certificate.
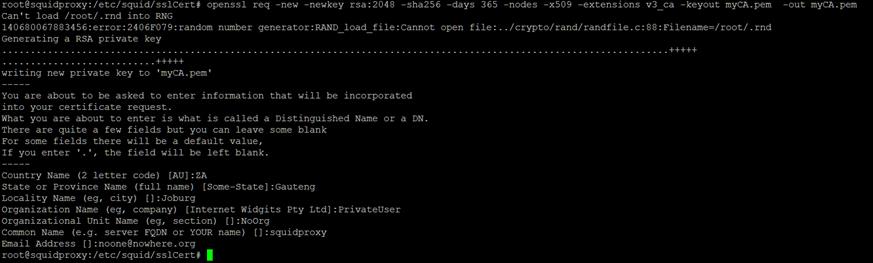
Execute the command in the screenshot above, keep in mind
that you will need to renew this certificate as often as the days specified in
the –days value. Fill in the info as requested.
Now we need to export the Certificate, so we can import in
on our User’s Pcs / Browsers.
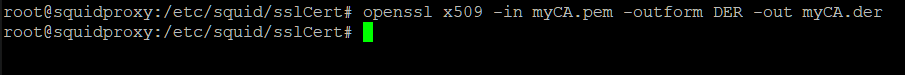
Type out & execute as per the screenshot above. Then
transfer the .der file to somewhere easily accessible. You will need to import
this into Trusted Root Certification Authorities in Windows / Firefox’s Trusted
Certificates Store etc… on each PC that uses the proxy.
Now we need to initialize Squids Certificate database, for
the dynamic certificate generation feature.
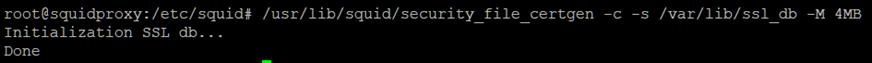
Type out the command above and Execute.
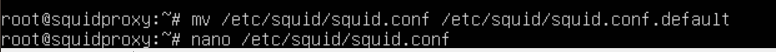
Type out and execute the commands in the screenshot above.
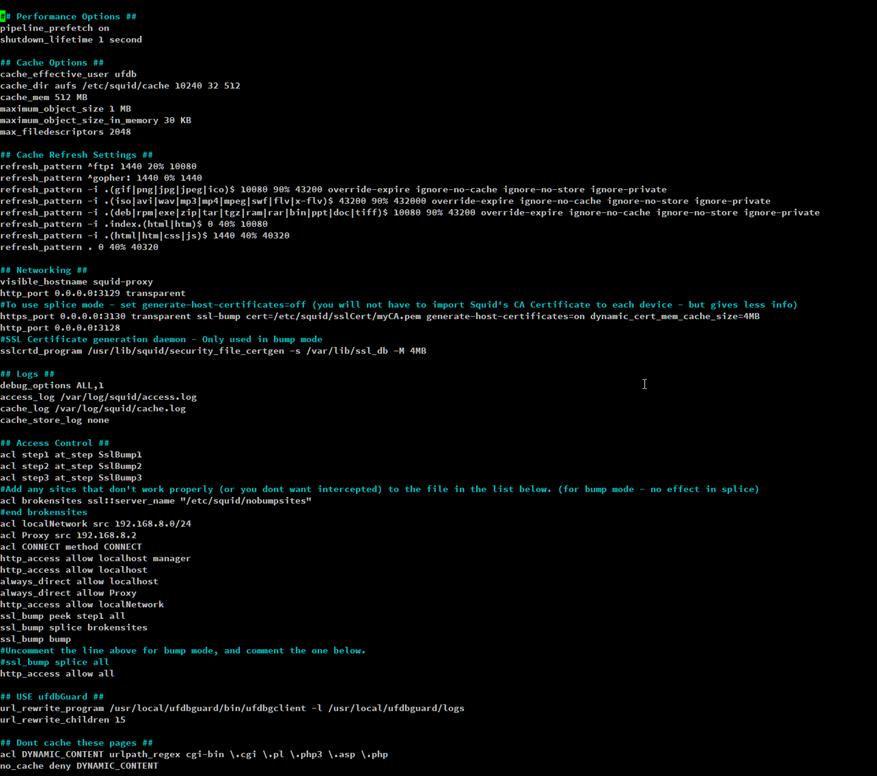
Type out the config above. Save & Exit.
Finally, we need to create the text file that will be used to store addresses of problematic sites (Some sites do not work correctly when their SSL connection is intercepted – for these we’ll use splice instead of bump. You also want to add internet banking sites to this list.)
Type touch /etc/squid/nobumpsites and press Enter.
Edit this file and add any urls you want to allow directly without intercepting their SSL connections to it.
The format should be (the . at the start is important):
.domain.com
Next Up: Installing & Configuring UFDBGuard

… [Trackback]
[…] Here you can find 79265 more Info on that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Read More Info here to that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Find More on that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Find More to that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Read More Info here to that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Read More to that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Here you can find 46311 additional Info on that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] There you can find 48351 more Information on that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Find More to that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Read More here to that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Read More on to that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Read More here to that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Find More on on that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Find More on that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Find More on to that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Here you will find 49911 more Information on that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Find More here to that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Read More Information here on that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Read More on that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Here you can find 66366 additional Info on that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] There you can find 54799 additional Information to that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Read More on on that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] There you will find 18406 additional Info on that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Here you can find 96156 additional Information to that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] There you can find 17518 more Information to that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Information to that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Find More on that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Information to that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Find More Info here on that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Information on that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Read More to that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Info to that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Read More here on that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Find More here to that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Read More Info here to that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Information on that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Find More Information here to that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] There you can find 23701 more Info on that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Info on that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Information to that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Read More to that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] There you can find 92806 additional Information on that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Find More on that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Info to that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Find More to that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Here you can find 69918 more Info on that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]
… [Trackback]
[…] Find More on to that Topic: cdss.co.za/how-to-setup-squid-as-a-transparent-ssl-proxy-with-site-filtering/ […]